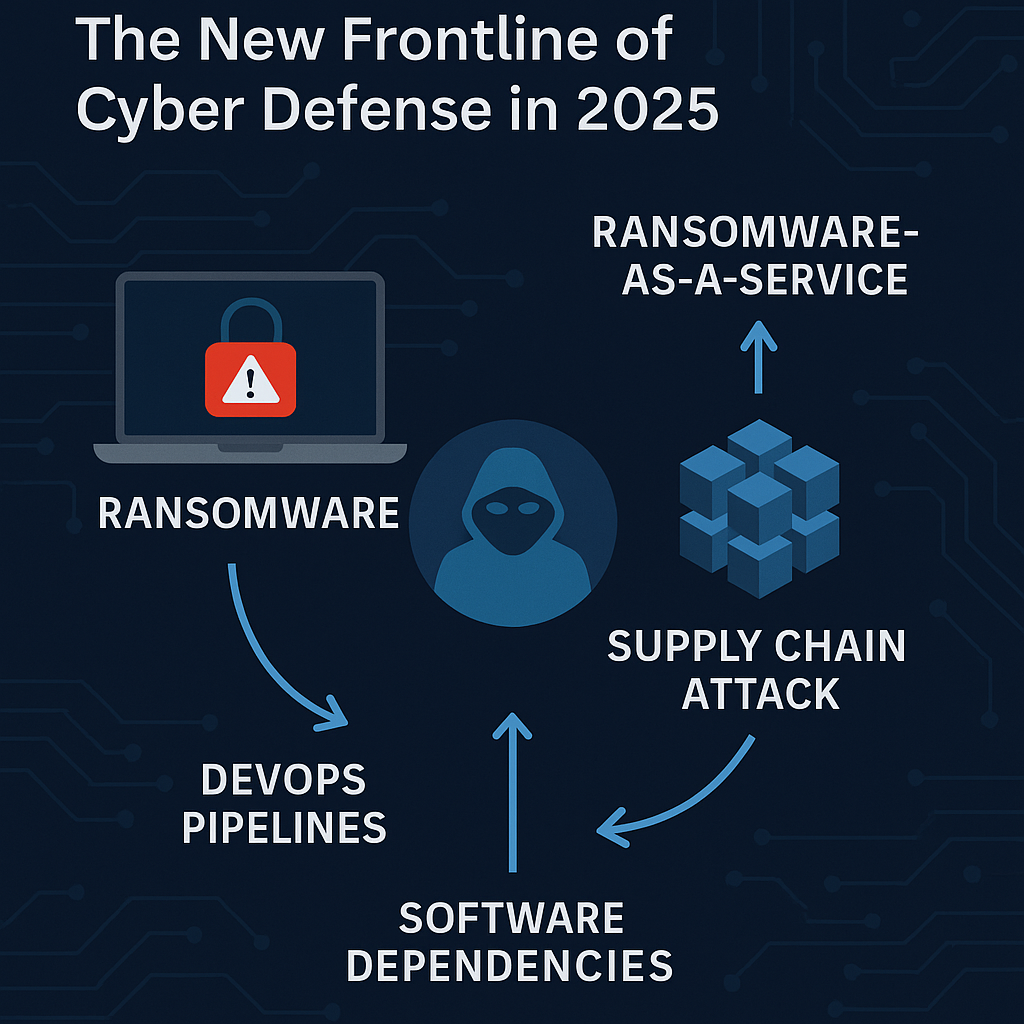
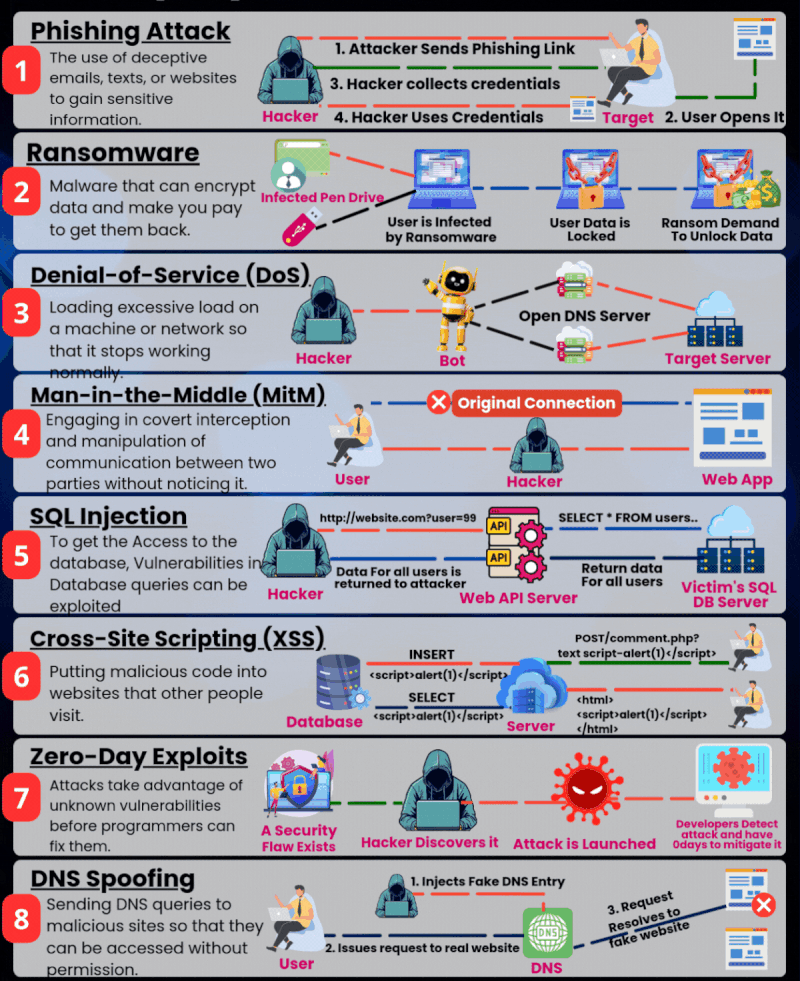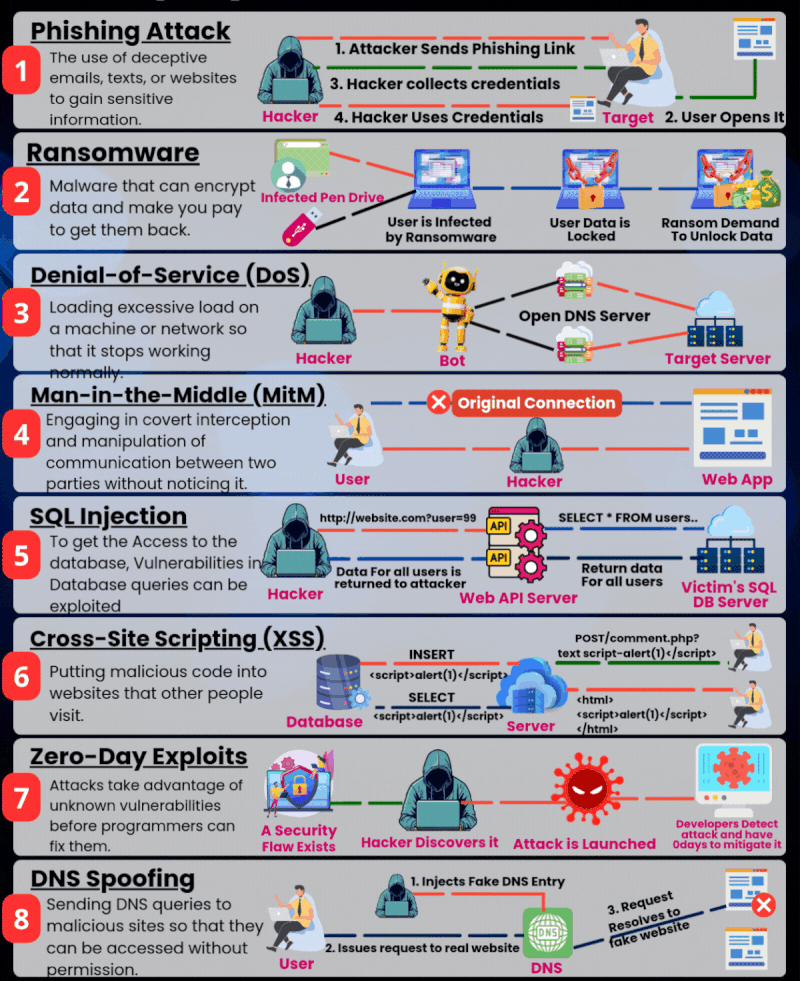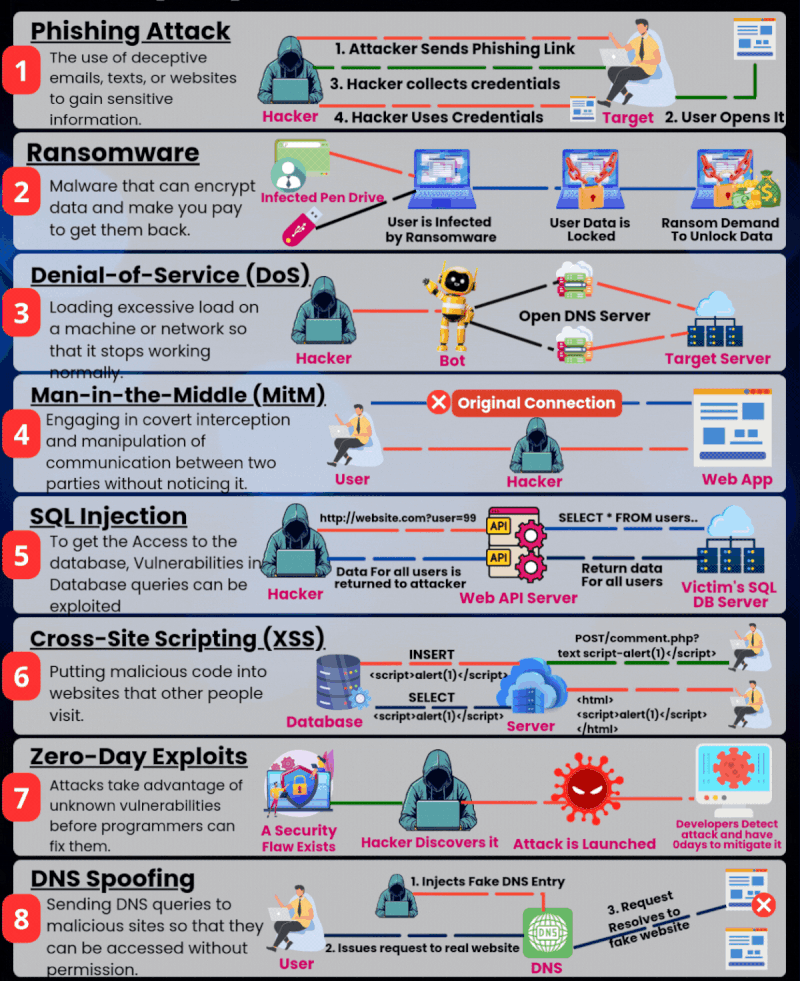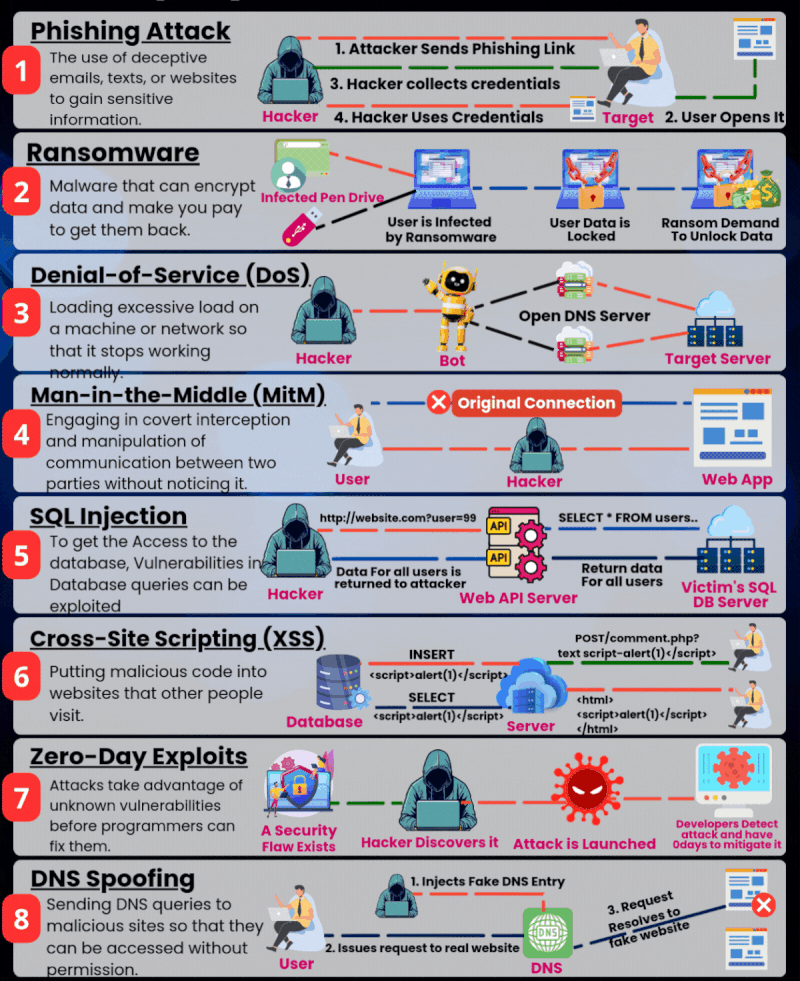
🚨 Kubernetes Update: NGINX Ingress Controller Is Deprecated — What This Means & How to Migrate
Kubernetes networking is entering a new era — and one of its oldest, most widely used components is stepping aside. For years, the open-source NGINX Ingress Controller powered traffic for countless Kubernetes clusters.It became the default choice for developers, DevOps teams, and platform engineers.If you ran Kubernetes, chances are… you deployed NGINX Ingress too. But … Read more