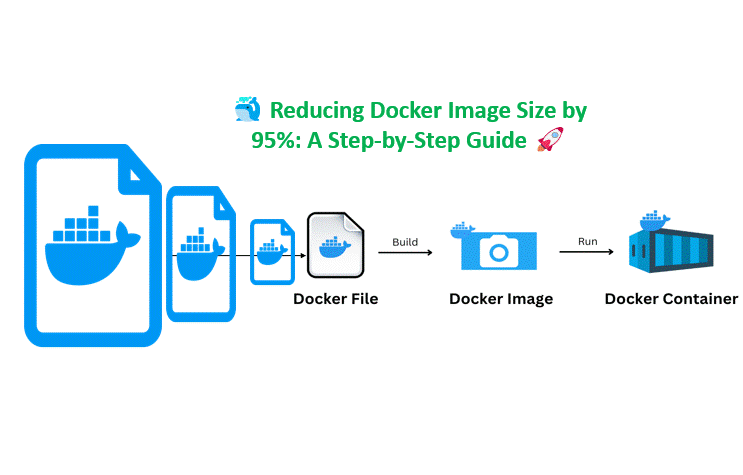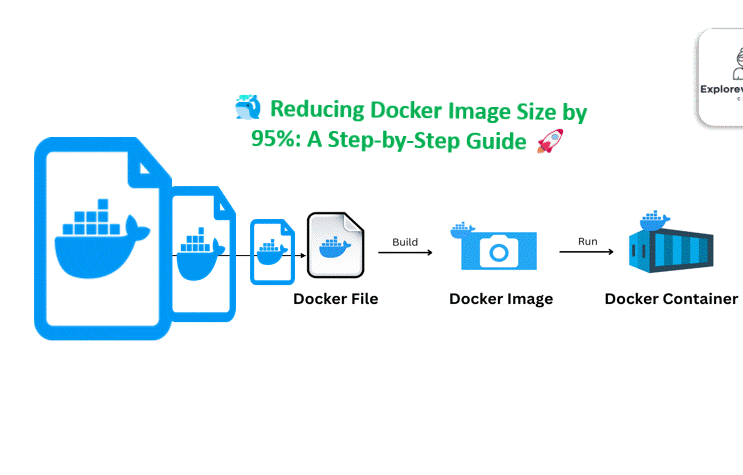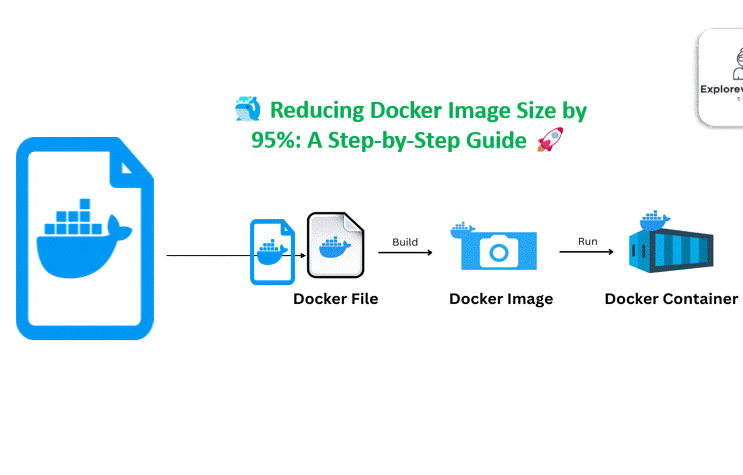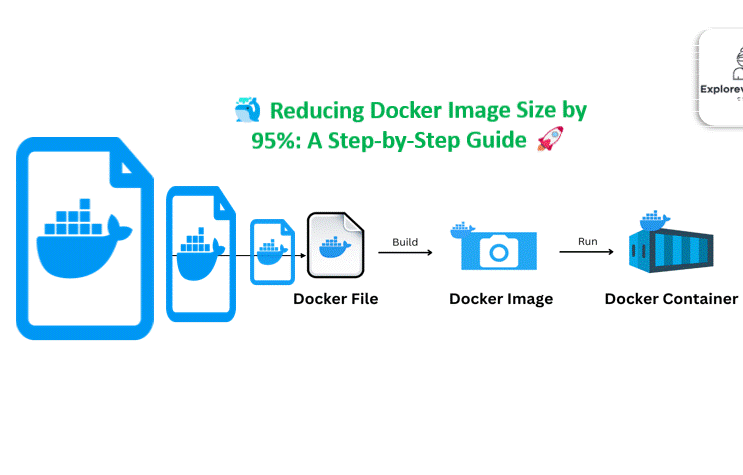
DevSecOps Mistakes Companies Never Admit: The Hidden Gaps That Break Security Pipelines
🚨 Introduction: The Dirty Secret of “Secure” Pipelines Every company today says, “We do DevSecOps.”But the truth? Most only pretend. Security tools are integrated in name, but not in behavior.Scans run without being enforced, reports are ignored, and secrets float across pipelines like unsecured luggage in an airport. In real Indian enterprise environments — from … Read more