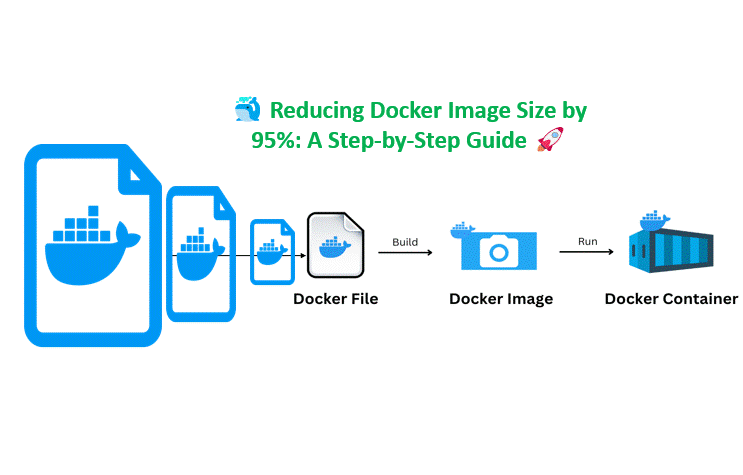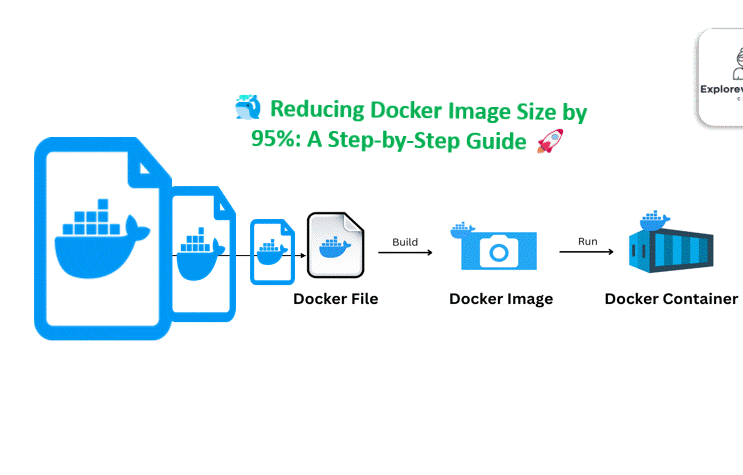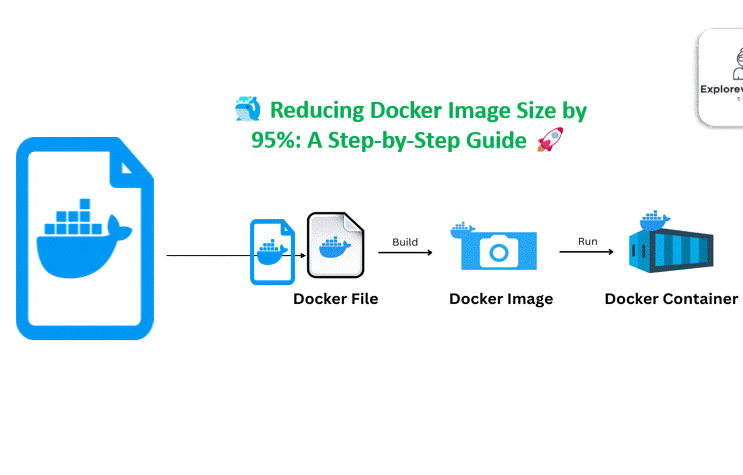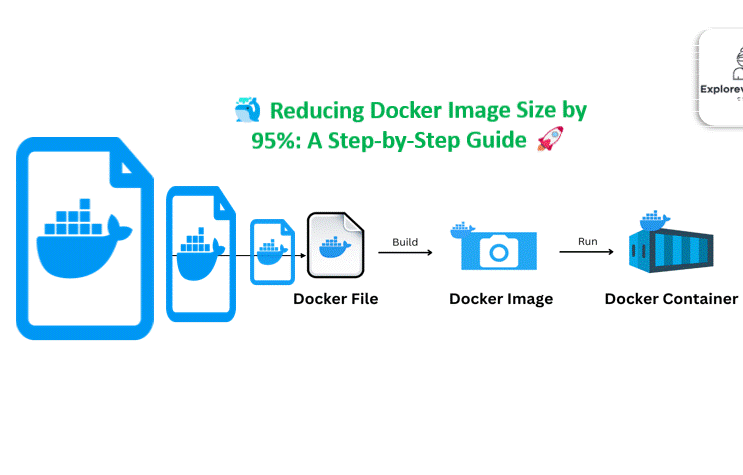
In the fast-paced world of DevOps, optimizing Docker images is crucial for ensuring efficient, secure, and rapid deployments. Bloated images can lead to longer build times, increased attack surfaces, and unnecessary resource consumption. Here’s a comprehensive guide to refining your Docker images, making them leaner and more secure.
1. 🏗️ Utilize Multi-Stage Builds
Multi-stage builds allow you to separate the build environment from the runtime environment, ensuring that only the necessary artifacts are included in the final image.
Example:
dockerfile# Stage 1: Build
FROM node:14 AS build
WORKDIR /app
COPY package.json package-lock.json ./
RUN npm install
COPY . .
RUN npm run build
# Stage 2: Production
FROM node:14-slim
WORKDIR /app
COPY --from=build /app/dist ./dist
CMD ["node", "dist/index.js"]
By compiling your application in one stage and transferring only the essential files to the production stage, you reduce the final image size and potential vulnerabilities.
2. 🧱 Choose Minimal Base Images
Selecting lightweight base images can significantly decrease your Docker image size and reduce the attack surface.
Options:
alpine(~5MB): A security-oriented, lightweight Linux distribution.distroless: Contains only your application and its runtime dependencies, omitting package managers and shells.
Example:
dockerfileFROM python:3.9-slim
Using minimal base images ensures faster deployments and enhanced security.
3. 🧠 Optimize Layer Caching
Docker caches layers to speed up builds. By ordering your Dockerfile instructions from least to most frequently changing, you can maximize cache efficiency.
Example:
dockerfileCOPY requirements.txt ./
RUN pip install -r requirements.txt
COPY . .
In this setup, if only the application code changes, Docker can reuse the cached layer for installing dependencies, accelerating the build process.
4. 🧹 Minimize Layers
Each instruction in a Dockerfile creates a new layer. Combining commands can reduce the number of layers, leading to smaller images.
Instead of:
dockerfileRUN apt-get update
RUN apt-get install -y package1
RUN apt-get install -y package2
Use:
dockerfileRUN apt-get update && apt-get install -y package1 package2
This approach not only reduces the number of layers but also ensures that temporary files are removed within the same layer, keeping the image clean.
5. 🔒 Avoid Running as Root
Running containers as the root user can expose your application to security vulnerabilities. It’s best practice to create a non-root user and switch to that user.
Example:
FROM node:14-slim
RUN useradd -m myuser
USER myuser
WORKDIR /app
COPY --from=build /app/dist ./dist
CMD ["node", "dist/index.js"]
This ensures that even if an attacker gains access to the container, they have limited permissions.
6. 🛡️ Scan Images for Vulnerabilities
Regularly scanning your Docker images helps identify and mitigate security risks. Tools like Trivy can automate this process.
Example:
trivy image your-image-name:latest
This command scans the specified image for known vulnerabilities, ensuring that your deployments remain secure.
7. 🧽 Keep It Clean
Ensure your Docker images are free from unnecessary files and outdated packages.
- Update base images regularly to incorporate the latest security patches.
- Remove unused packages and temporary files.
- Use
.dockerignoreto exclude files and directories that aren’t needed in the final image.
Example .dockerignore:
nginxnode_modules
*.log
.git
By keeping your images clean, you reduce their size and potential vulnerabilities.
📌 Conclusion
Optimizing Docker images is not just about reducing size; it’s about enhancing performance, security, and efficiency. By following this 7-step checklist, you ensure that your containers are lean, secure, and production-ready