Kubernetes Security in Real Production: A Practical DevSecOps Guide That Actually Works
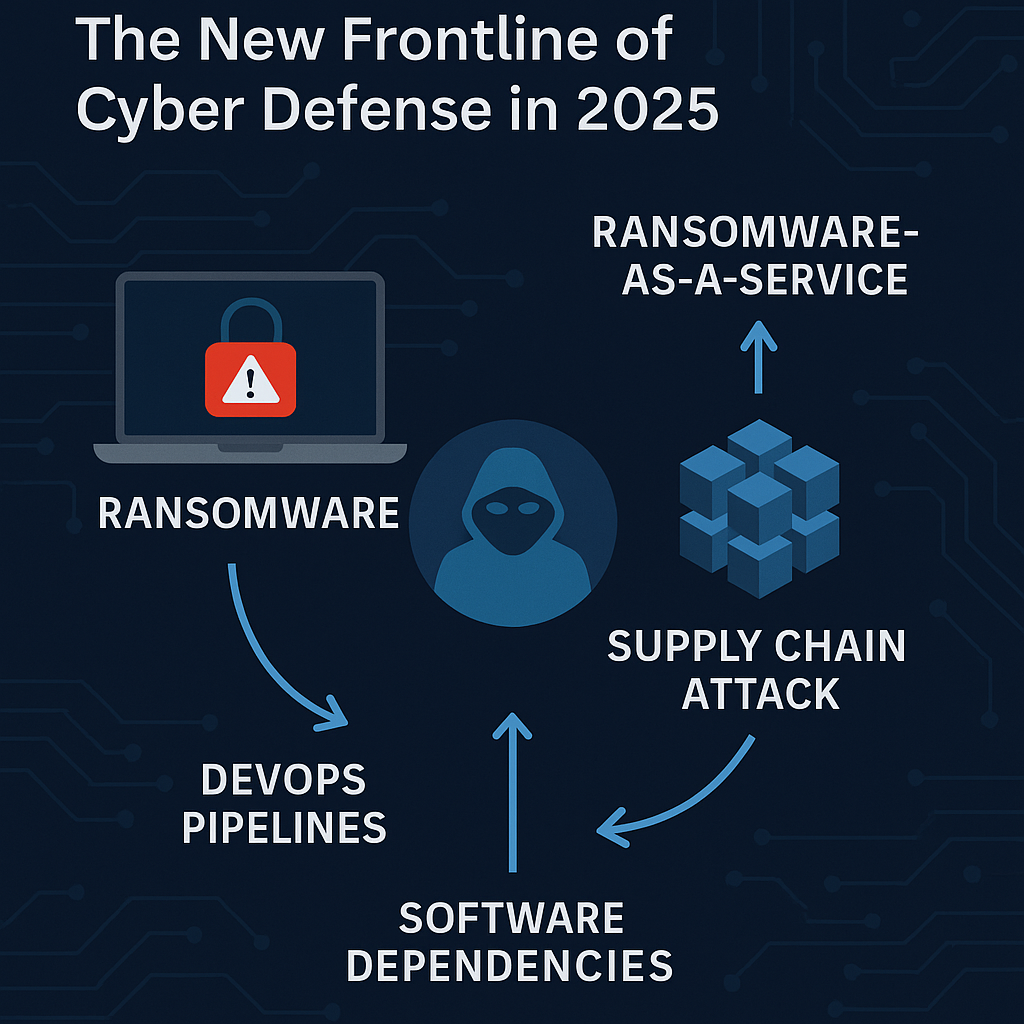
Let’s be honest — Kubernetes security isn’t just about turning on RBAC or running an image scan once in your CI pipeline.If that’s all you’re doing, you’re only covering the surface — not the real risks. In my experience, most Kubernetes breaches don’t happen because someone found an exotic zero‑day. They happen because of the … Read more