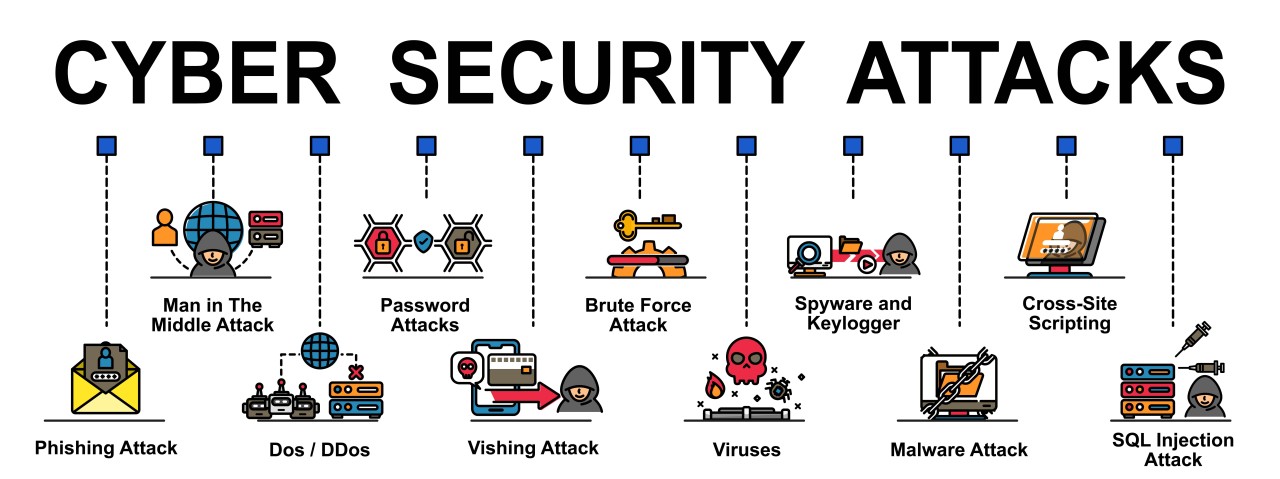
🦠 Types of Cyber Attacks
🦠 Viruses Description: Malicious software that attaches to clean files and spreads throughout a computer system. Impact: Can corrupt or delete data, and spread to other systems. 💻 Malware Attack Description: Any software intentionally designed to cause damage to a computer, server, or network. Impact: Can lead to data theft, system damage, or unauthorized access. … Read more