🔍 Introduction
In 2025, credential theft remains the most exploited attack vector, accounting for nearly 40% of all breaches (Fortinet Threat Landscape Report, 2025). What’s more alarming is that once attackers gain access, they no longer stop at a single account — they use lateral movement to traverse cloud, Kubernetes, and CI/CD environments silently.
For DevOps and Cloud teams, this is a serious wake-up call. Secrets, tokens, and service accounts — the lifeblood of modern automation — have become prime targets.
Let’s explore how credential theft and lateral movement are evolving, and what you can do to prevent them in your infrastructure.
🧠 1. How Credential Theft Happens in Modern Pipelines
Credential theft has moved beyond phishing emails and weak passwords. Attackers now target:
- Hard-coded credentials in GitHub or container images
- Leaked tokens in CI/CD logs or misconfigured runners
- Cloud API keys stored in plaintext or exposed via IaC misconfigurations
- Stolen SSH keys from developer workstations or shared build agents
🔍 Fact: According to CrowdStrike’s 2025 Global Threat Report, 61% of cloud intrusions began with stolen credentials or API tokens.
Example Attack Chain:
- A DevOps engineer’s GitHub token leaks via a public repo.
- The attacker uses it to access the private CI pipeline.
- They inject malicious code into a container build job.
- The compromised container image is deployed to production.
Image:
🔄 2. Lateral Movement — The Silent Progression
Once inside, attackers rarely stay still. Using legitimate credentials, they move laterally through systems — often appearing as authorized users.
Common lateral techniques include:
- Reusing stolen tokens or SSH keys to pivot between clusters
- Exploiting over-permissive IAM roles (e.g.,
AdministratorAccess) - Enumerating connected services via metadata APIs (
169.254.169.254on AWS) - Escalating privileges through CI/CD service accounts
DevOps Example:
A compromised Jenkins controller can trigger jobs in ArgoCD, which deploy malicious workloads to Kubernetes clusters.
This is why “identity sprawl” — unmanaged service accounts and tokens — is a major risk in multi-cloud setups.
Image: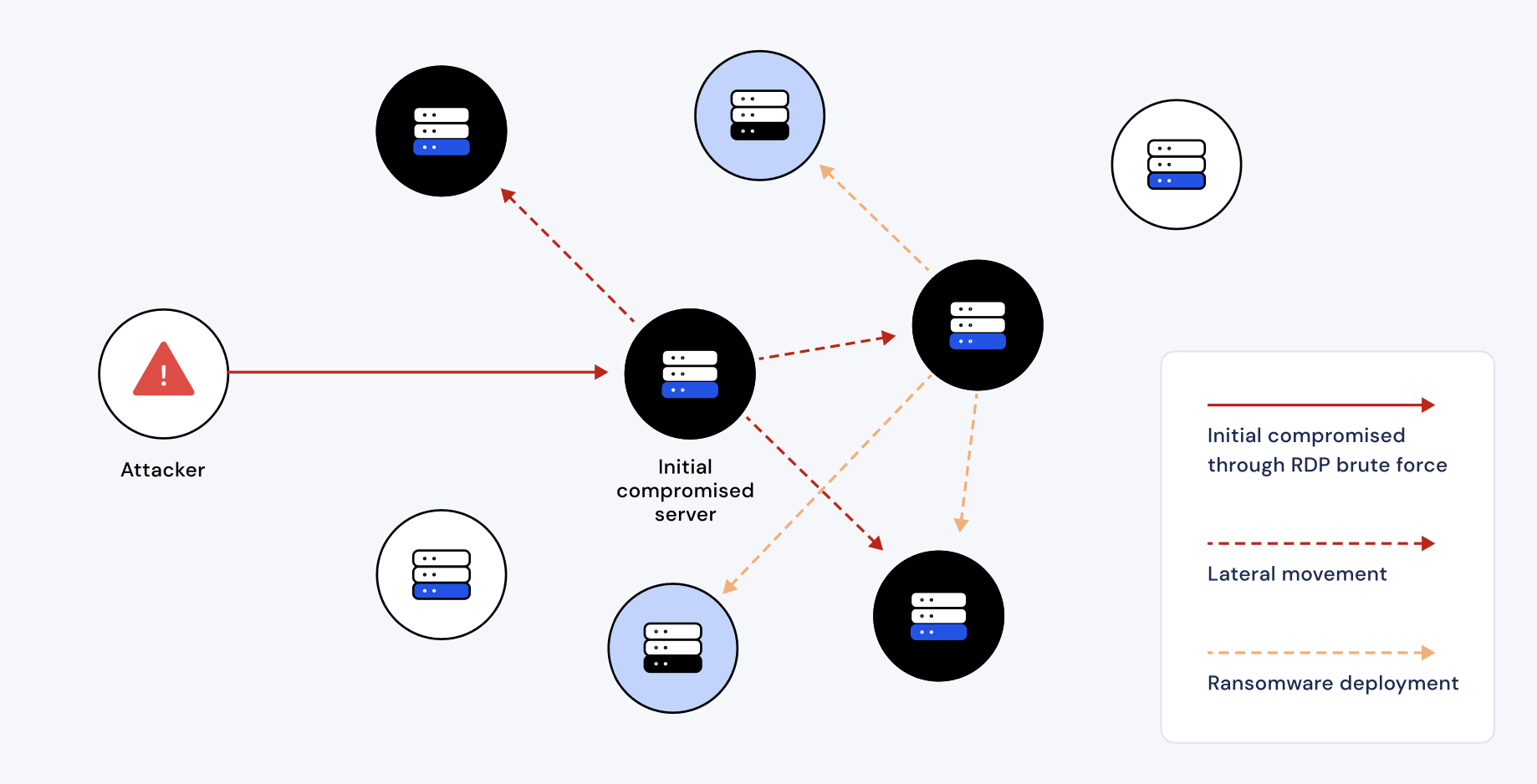
⚙️ 3. Why DevOps Environments Are Prime Targets
DevOps pipelines combine speed, automation, and access — a perfect storm for attackers.
- Continuous access: CI/CD systems often run with privileged credentials.
- Automation tokens: Build agents and bots require constant API access.
- Secret reuse: Credentials are often shared between environments.
- Visibility gaps: Security tools may not inspect pipeline-level secrets or build logs.
Common weak spots:
| Component | Risk | Example |
|---|---|---|
| Jenkins / GitLab CI | Leaked tokens | Plaintext credentials in environment variables |
| Kubernetes | Service account abuse | Default token not rotated |
| Terraform / IaC | Hardcoded secrets | AWS keys in .tfvars files |
| Container Registry | Insecure permissions | Public push access enabled |
Image:
🔐 4. How to Defend Against Credential Theft & Lateral Movement
To counter these threats, DevOps and Cloud teams must build identity-centric security at every stage of the software lifecycle.
🔸 Secrets Management
- Use tools like HashiCorp Vault, AWS Secrets Manager, or Kubernetes External Secrets.
- Rotate secrets automatically and use short-lived credentials.
- Avoid storing secrets in version control or environment variables.
🔸 Token Hygiene
- Enforce OAuth scopes (least privilege).
- Use OIDC Federation instead of long-lived tokens for CI/CD pipelines.
- Monitor for token misuse with tools like Falco or Sysdig Secure.
🔸 Lateral Movement Prevention
- Implement network segmentation and namespace isolation in Kubernetes.
- Use identity-based access control (IAM/RBAC) everywhere.
- Apply Zero Trust principles — verify every action, every time.
🔸 Monitoring & Forensics
- Use Audit Logs (AWS CloudTrail, Kubernetes Audit API) to trace movements.
- Correlate activity across systems via SIEM tools (Splunk, Elastic).
- Detect abnormal access patterns using AI/behavioral analytics.
Image:
🧭 5. Real-World Case: DevOps Token Reuse Incident
In early 2025, a Fortune 500 cloud provider suffered a breach after an internal CI/CD token was reused across multiple pipelines. The attacker, once inside one project, pivoted to production environments through shared build agents.
Post-incident review showed:
- The same secret was used in five different environments.
- IAM roles allowed full S3 and ECR access.
- No automated rotation or anomaly alerts were configured.
Lesson:
A single leaked token can become a chain-reaction breach if lateral controls are missing.
🧾 Key Takeaways
- Credentials are the new perimeter — treat them like crown jewels.
- DevOps pipelines must be zero-trust by design, not by policy.
- Adopt continuous secrets scanning and rotation practices.
- Detect and block lateral movement early using behavioral AI and microsegmentation.

