Source: outoftheboxtech.in
In today’s hyper-connected world, cyber threats are more sophisticated than ever. 🚨 Whether you’re a business owner, tech enthusiast, or casual internet user, understanding how these attacks work can help you stay one step ahead of cybercriminals. Let’s dive into 8 of the most common and dangerous cyberattacks to watch out for in 2025 👇

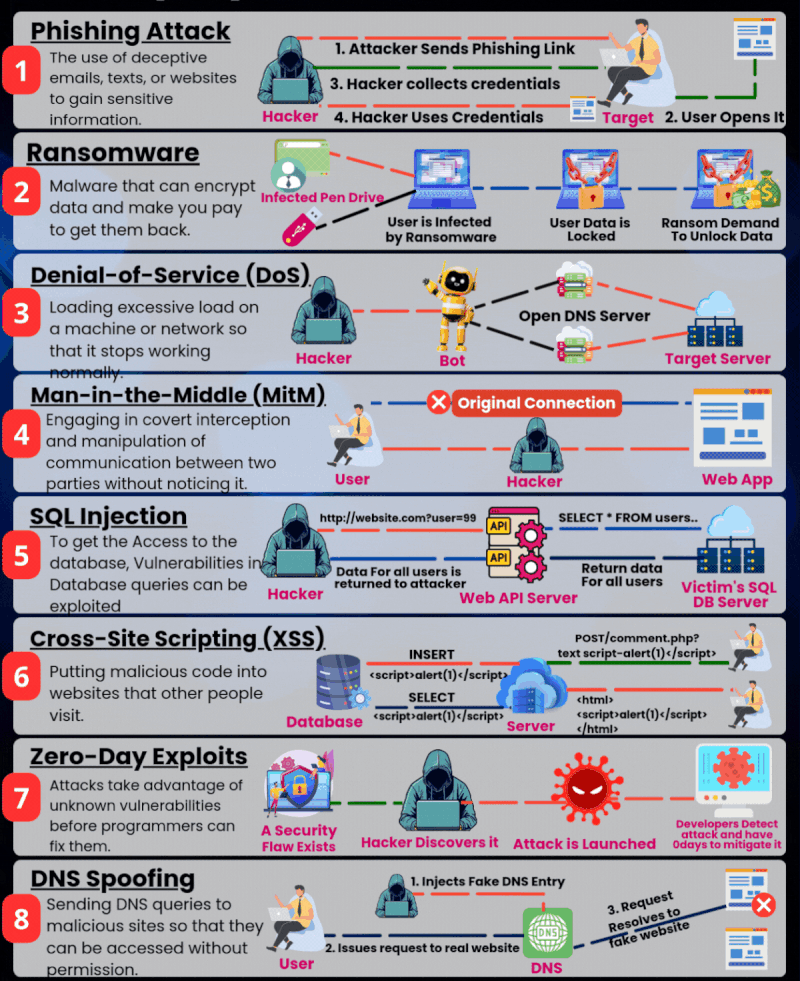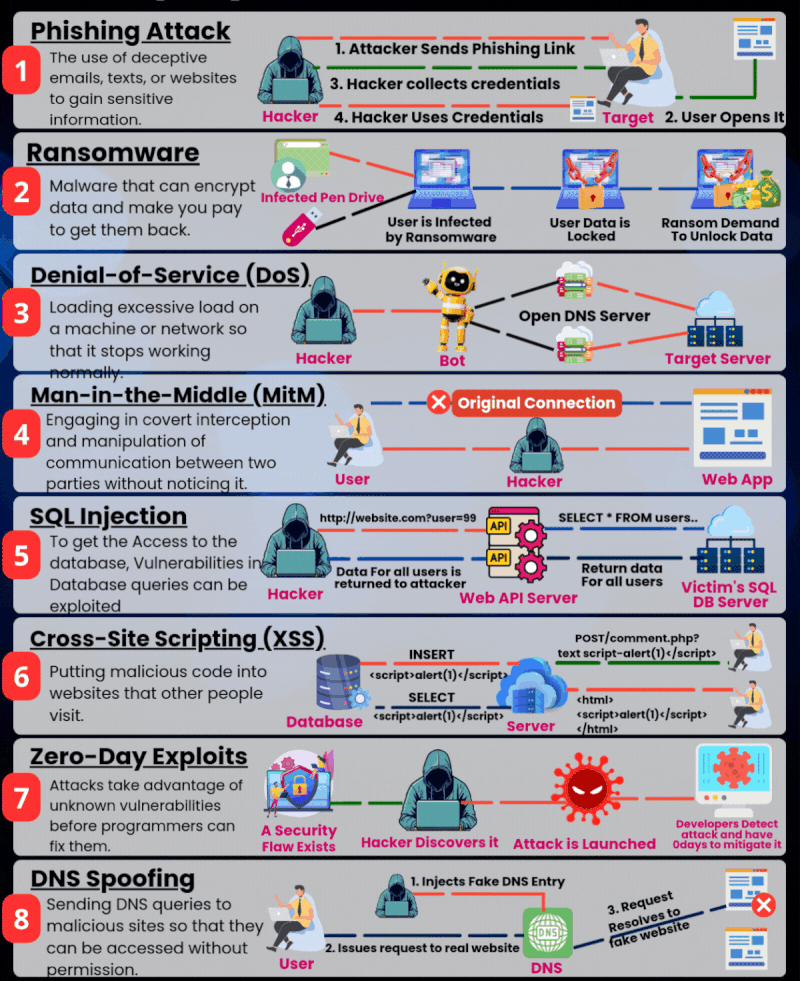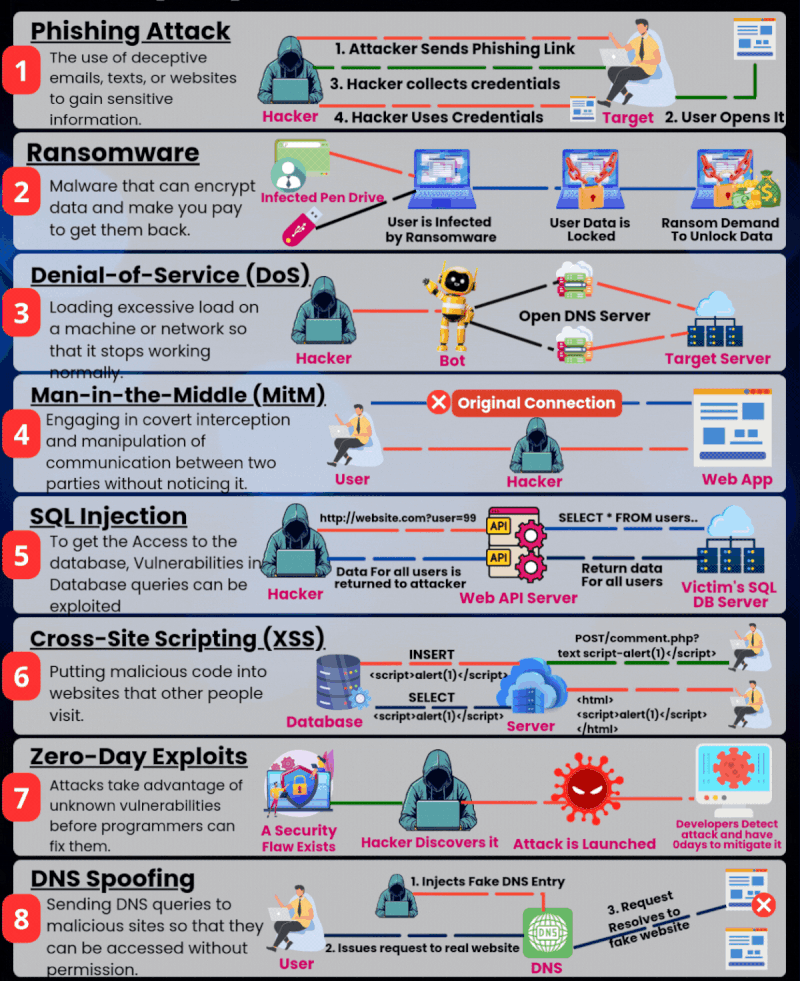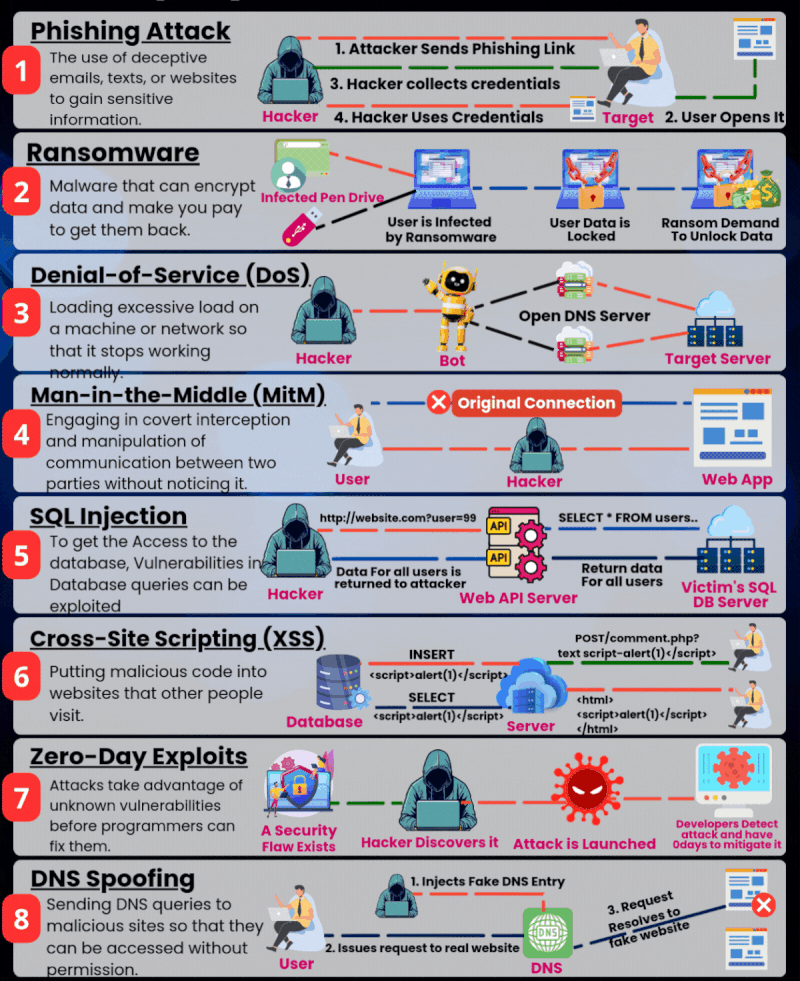
1️⃣ Phishing Attack 🎣📩
What it is: A deceptive attempt to steal sensitive information like passwords or credit card details via fake emails, texts, or websites.
How it works:
- Attacker sends a malicious link disguised as a legit one
- The target clicks it and enters personal details
- Hacker collects the data and uses it to gain access
👉 Tip: Always double-check URLs and sender addresses. When in doubt, don’t click!
2️⃣ Ransomware 🛑💰
What it is: Malware that locks or encrypts your files and demands a ransom to restore access.
How it works:
- Spreads via infected USBs, emails, or websites
- Once activated, your data becomes inaccessible
- A ransom message appears, demanding payment (usually in crypto)
👉 Tip: Backup data regularly and keep antivirus software up to date.
3️⃣ Denial-of-Service (DoS) ⚙️🚫
What it is: An attack that overwhelms a server or network with traffic, making it unavailable to users.
How it works:
- Hackers use bots to flood the target server
- The system crashes or becomes unresponsive
- Users are denied access to services
👉 Tip: Use firewalls and network traffic monitoring tools to prevent DoS attacks.
4️⃣ Man-in-the-Middle (MitM) 👥🔍
What it is: A sneaky attack where a hacker intercepts communication between two parties.
How it works:
- The hacker positions themselves between the user and the server
- They capture data like login credentials or credit card numbers
- The victim remains unaware of the interception
👉 Tip: Always use websites with HTTPS and avoid public Wi-Fi without a VPN.
5️⃣ SQL Injection 🧠📊
What it is: A code injection technique that exploits vulnerabilities in database queries.
How it works:
- The attacker inputs malicious SQL code via a form field or URL
- The code tricks the system into executing unauthorized commands
- Sensitive data is exposed or manipulated
👉 Tip: Validate user input and use prepared statements in SQL queries.
6️⃣ Cross-Site Scripting (XSS) 💬💣
What it is: Injecting malicious scripts into websites that are viewed by other users.
How it works:
- Hacker inserts a script into a comment or form
- Other users load the infected page and the script executes in their browser
- The hacker can steal cookies, session tokens, or other data
👉 Tip: Sanitize and validate all input fields and use Content Security Policies.
7️⃣ Zero-Day Exploits 🕳️🛠️
What it is: Attacks that exploit software vulnerabilities unknown to developers.
How it works:
- A hacker discovers a security flaw
- They launch an attack before the developer can patch it
- Victims are blindsided with no available fix
👉 Tip: Use auto-updates, patch management tools, and threat detection systems.
8️⃣ DNS Spoofing 🌐🎭
What it is: Redirecting users from legitimate websites to fake ones.
How it works:
- Hacker injects a fake DNS entry
- Your device resolves to the malicious site instead of the real one
- Personal data can be stolen or malware installed
👉 Tip: Use secure DNS services and enable DNSSEC where possible.