In modern software delivery, integrating security into your CI/CD pipeline is no longer optional — it is critical. DevSecOps pipelines aim to embed security at every stage, ensuring quality, compliance, and resilience. Let’s walk through a real Jenkins pipeline that exemplifies a fully-automated DevSecOps workflow, with each stage designed for code quality, vulnerability detection, and secure delivery.
✅ 1. Build Checkout
What Happens:
Pulls the latest codebase from the configured source control management system (e.g., GitHub, GitLab, Bitbucket).
Why It Matters in DevSecOps:
Ensures a secure and verified source is used as the foundation of the build. Git hooks or signed commits may also be validated here to maintain supply chain integrity.
🛠️ 2. Build Now
What Happens:
Builds the project using tools like Maven or Gradle. Compiles code and packages it into an executable format (e.g., JAR, WAR, Dockerfile context).
DevSecOps Integration:
Build processes are monitored for unauthorized dependency injection or malformed artifacts. Build reproducibility is enforced using version locks (pom.xml, package-lock.json).
🔍 3. Code Quality Scan
Tooling: SonarQube, PMD, SpotBugs
What Happens:
Static code analysis is performed to detect:
- Code smells
- Potential bugs
- Maintainability issues
- Security vulnerabilities (e.g., SQL injection patterns)
DevSecOps Value:
Early detection of security vulnerabilities and anti-patterns during code authoring ensures faster remediation and better developer feedback loops.
🧪 4. Synk-Test (Dependency Vulnerability Scan)
Tooling: Snyk, OWASP Dependency-Check
What Happens:
Analyzes all dependencies (including transitive) to check against known CVEs. Produces a detailed report on vulnerable components.
DevSecOps Value:
Addresses Software Composition Analysis (SCA), a key component of supply chain security, and prevents the usage of risky open-source libraries.
🐳 5. Vulnerability Scan – Docker
Tools: Trivy, OPA Conftest, OWASP Dependency-Check
What Happens:
Scans the built Docker image for:
- OS-level CVEs
- Misconfigurations
- Insecure default settings
- Outdated libraries
OPA policies validate container settings against enterprise rules.
DevSecOps Impact:
Ensures container images are secure by design, blocking any image that doesn’t meet organization policies.
🏷️ 6. Rename & Move Build
What Happens:
Renames the artifact (e.g., adds a version tag or commit hash) and moves it to a staging area.
Why Important:
This helps in traceability, which is crucial for post-incident analysis and audit trails in secure environments.
🔔 7. Slack Notification
What Happens:
Pipeline status (success/failure) is communicated to stakeholders or team channels.
DevSecOps Use Case:
Immediate alerting in case of vulnerability detection or failed deployment prevents delays and helps in proactive mitigation.
🗃️ 8. Registry Approve
What Happens:
Gate approval before pushing image to a container registry like Harbor.
Security Focus:
Manual or automated policies prevent unverified images from being published, reducing the chance of image poisoning or privilege escalation.
🐋 9. Docker Image Build & Push
What Happens:
Builds and tags the Docker image. Pushes to Harbor (or other registry) if validations pass.
DevSecOps Value:
Harbor supports vulnerability scanning, role-based access control (RBAC), and image signing — essential features for secure image management.
🔐 10. Vulnerability Scan – Kubernetes
Tools: KubeSec, Trivy, OPA
What Happens:
- KubeSec validates security contexts (e.g.,
runAsNonRoot) - Trivy scans Kubernetes manifests for CVEs
- OPA ensures policy compliance (e.g.,
no hostPath,readOnlyRootFilesystem)
Security Enforcement:
Validates deployment configurations before they reach the cluster, enforcing least privilege and hardening the attack surface.
🚀 11. K8s Deployment – DEV
What Happens:
Deploys the application to a DEV namespace in Kubernetes. Validates rollout status.
Why It’s Secure:
Deploying to a dedicated, isolated environment first helps catch issues early and protects the production environment from unverified deployments.
🧪 12. Integration Tests – DEV
What Happens:
Runs end-to-end and integration tests in the DEV environment using tools like Postman/Newman or custom bash scripts.
DevSecOps Relevance:
Ensures that feature changes and security patches don’t introduce new regressions. All endpoints and workflows are tested against expected behavior.
🛡️ 13. OWASP ZAP – DAST
Tooling: OWASP ZAP (Zed Attack Proxy)
What Happens:
Performs Dynamic Application Security Testing (DAST) on the running application.
Capabilities:
- Passive and active vulnerability scanning
- Testing for XSS, CSRF, open redirects, etc.
- Custom authentication scripts
Impact:
Catch runtime vulnerabilities before going live. This is critical for web-facing applications.
🚦 14. Prompt to PROD
What Happens:
Manual approval step to proceed with production deployment.
Security Role:
Adds human validation as an extra safety barrier before pushing to the production environment — ensuring 4-eyes principle compliance.
🧰 15. K8s CIS Benchmark
Tools: kube-bench, CIS Validator
What Happens:
Checks Kubernetes components like etcd, kubelet, and control plane against CIS Kubernetes Benchmark.
Why Important:
Hardens your Kubernetes infrastructure and ensures compliance with industry-standard configurations.
🚀 16. K8s Deployment – PROD
What Happens:
Deploys the final, verified application to the production namespace.
DevSecOps Alignment:
Uses RBAC-restricted service accounts, encrypted secrets, and monitored rollout. Promotes continuous security posturing in live environments.
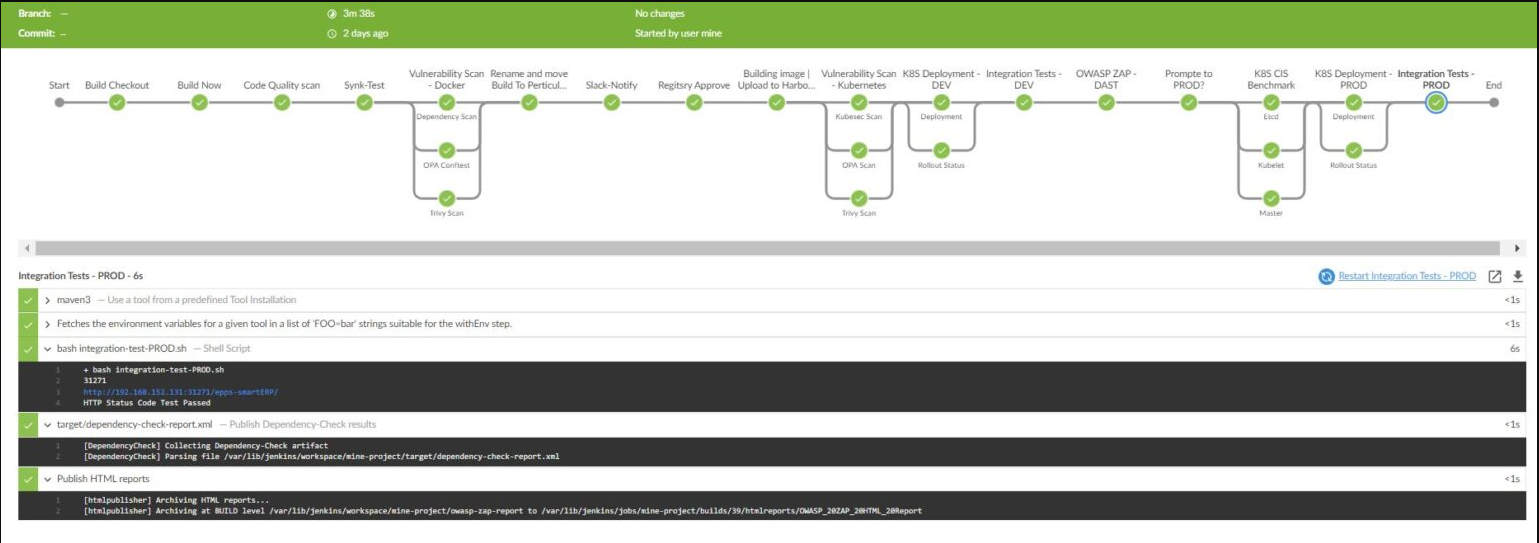
🧪 17. Integration Tests – PROD
What Happens:
Final round of integration testing is run on production (canary/blue-green/staged environments) using:
bash integration-test-PROD.sh
URL: http://192.168.152.131:31271/epps-smartERP/
HTTP Status Code Test Passed ✅
Why Important:
Confirms service availability and application behavior post-deployment.
📊 Reports Generated
- Dependency-Check Report: Scanned and archived as
dependency-check-report.xml - OWASP ZAP HTML Report: Saved for security audit and further analysis
Security Insight:
Archiving reports ensures that teams can trace back vulnerabilities and audit every stage for compliance (e.g., ISO 27001, SOC2).
🧠 Final Thoughts
This Jenkins pipeline is a model DevSecOps implementation. It doesn’t just automate CI/CD — it embeds security, compliance, and governance across the SDLC.
By integrating:
- Static code analysis (SAST)
- Software Composition Analysis (SCA)
- Dynamic security testing (DAST)
- Container and Kubernetes hardening
- Continuous monitoring and alerting
…you ensure rapid delivery with zero compromise on security. 🔐🚀

